Generative AI technology is constantly evolving and can be considered one of the most representative topics of 2023. From designing presentations and automatically generating art using commands to building and deploying AI models with code, the potential applications and development of AI in the future are highly anticipated. However, while new technologies bring convenience to businesses, they also come with potential cybersecurity risks. Misuse of these technologies can lead to concerns about data access and leaks, turning the advantages of generative AI into threats. In this series on “Potential Cybersecurity Risks in the Cloud Era,” we will explore how to ensure data security when adopting these new technologies to assist businesses in their development.
Table of Contents
Table of Contents
Widespread Applications of Generative AI Increase Cloud Security Risks
ChatGPT is a natural language generation tool that, according to a survey by ResumeBuilder.com, has allowed nearly 25% of companies to save up to $75,000 in costs. This implies that certain job functions within organizations may change in the future due to the more powerful applications of ChatGPT, potentially reshaping how businesses establish economic models.
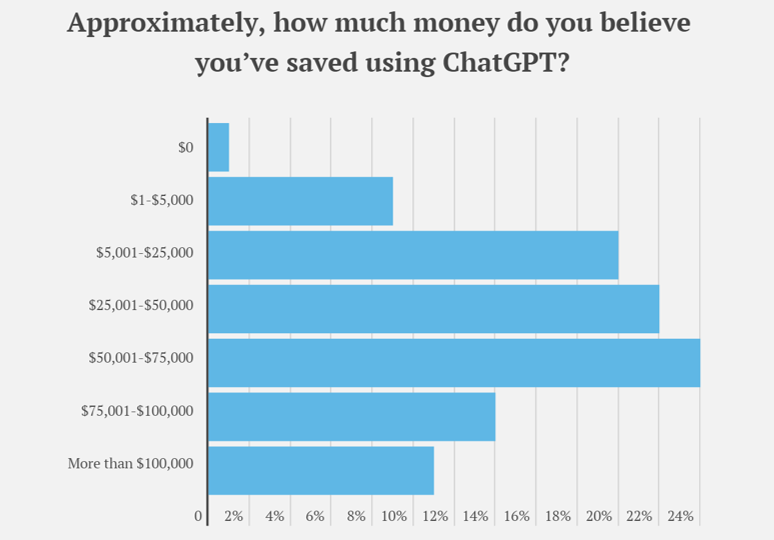
However, despite the benefits of using ChatGPT and other generative AI tools for streamlining processes and improving efficiency, businesses may unintentionally compromise their cybersecurity. A survey conducted by Malwarebytes, an antivirus software company, revealed that over 80% of companies are concerned about the cybersecurity risks associated with generative AI tools. For example, some individuals may use ChatGPT to train on highly sensitive company data, and hackers can now enhance their attacks using generative AI, such as guessing passwords to breach applications and steal data.
Preventing Cybersecurity Threats in the AI Era: Cloud Security Guidelines
In the face of rapidly evolving cyber threats and the development of generative AI, even professional software service providers struggle to defend against cybersecurity threats. Circleci, a CI/CD integration platform that enables DevOps practices for businesses, experienced an incident where an employee with permissions to create tokens in the production environment was targeted. Unauthorized third-party hackers exploited various techniques to access parts of the database, stealing customer environment variables, tokens, and keys, resulting in losses for both parties.
In light of such incidents, “Security Intelligence,” a well-known cybersecurity blog, proposes five key strategies to maintain the security of your cloud environment in the AI era:
Strengthen Access Control Management
Implement the principle of “least privilege” by establishing comprehensive access rules for different departments within the system. Enable two-factor authentication (2FA) to enhance access control. Key applications like AWS Identity Access Management (IAM) and enabling Multi-Factor Authentication (MFA) help mitigate the risk of excessive permissions leading to data leaks.
Utilize Encryption Practices
Adhere to encryption standards for both data at rest and in transit to prevent unauthorized access. Properly manage encryption keys, including regular rotation and replacement, as a critical task in safeguarding data in the AI era. AWS Key Management Service (KMS) is a fully managed service that automates key rotation and generation for data protection.
Adopt Cloud-Native Security Strategies
Embrace the “shared responsibility model” and ensure that your organization fulfills its responsibilities within this model. Implement cloud-native security strategies and combine them with the shared responsibility framework using AWS Security Hub’s centralized alerting system to enhance security.
Implement “AI for AI” Security Monitoring and Alerting Systems
When facing AI-powered cyberattacks, using “AI for AI” is the best strategy. Employ AI-enabled alert detection systems to strengthen monitoring and provide real-time alert analysis. For applications hosted on AWS, consider using Amazon GuardDuty to visualize threat detection and automate incident response through machine learning.
Regular Vulnerability Scanning and Penetration Testing
Conduct regular vulnerability scans and penetration tests of your cloud environment to identify potential threats. Tools like Amazon Inspector offer automated vulnerability scanning, while enabling ElasticSearch for log analysis helps uncover hidden cloud security weaknesses.
As AI technology matures, various types of cyber threats continue to evolve, and AI itself may be used as a weapon to steal critical information from enterprise cloud environments. However, businesses have options to proactively mitigate these risks. In the future, we can expect to see a range of “AI for AI” security tools and heightened protection and applications in areas such as “data privacy,” “regular audits,” and “resource management” to confidently address various cloud security challenges in the age of generative AI.
If your business is looking to enhance cloud security or is facing challenging cloud security issues in the AI era, Nextlink Technology has a professional cybersecurity team and solutions to assist you in comprehensive cloud data security through cloud hosting and 24/7 monitoring!





