“Hackers are moving to the cloud too,” this is a situation many businesses are experiencing recently. There have been reports indicating that some groups are using phishing emails under the guise of membership expiration on well-known e-commerce websites. They exploit failed automatic credit card payments as a reason and step by step, steal members’ personal information and privacy. Not only that, a hacker mission called “SCARLETEEL Operation” targets containerized workloads, stealing data from cloud environments and causing significant losses for companies.
Nextlink introduces a new topic series – “Potential Security Risks in the Cloud Era”. It analyzes recent rampant cloud security incidents, dissects hacker techniques, and provides comprehensive trend solutions, allowing you to enhance your cloud security resilience!
Table of Contents
Table of Contents
Cloud Environments Vulnerable to Hacker Attacks? Identify the Weak Points Here!
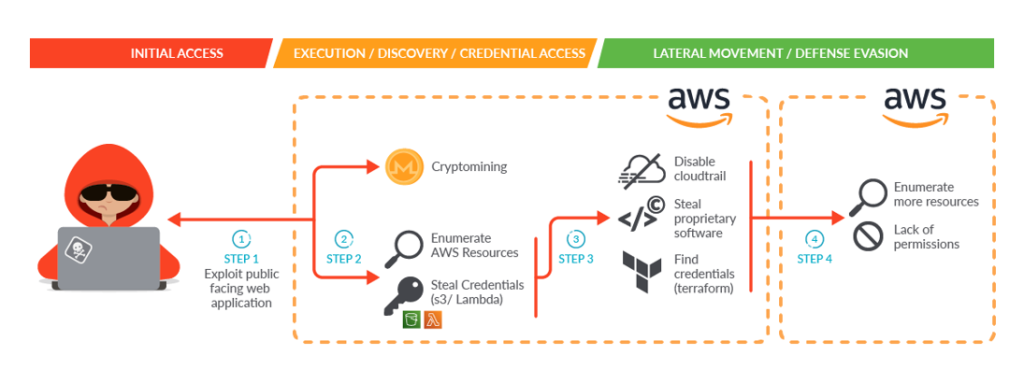
Recent investigations reveal a 56% increase in network attacks within cloud environments compared to last year, indicating a growing trend in cloud security breaches. The recent SCARLETEEL operation serves as a prime example of hackers infiltrating AWS cloud environments. Attackers exploit publicly accessible k8s clusters managed within AWS accounts to gain unauthorized access. Once authorized, they activate cryptocurrency mining software to generate profits. Moreover, attackers obtain credentials to enumerate resources, pilfer credentials stored in Amazon S3 and AWS Lambda, enabling hackers to exploit vulnerabilities, resulting in significant losses for enterprises.
Furthermore, hackers communicate stolen credentials with AWS APIs, enumerate accounts, and leak collected data, bypassing detection by forcibly stopping AWS CloudTrail logging. These actions allow hackers to access a company’s internal patented data and confidential information. This cloud network kill chain dissects the attack into seven steps, progressively infiltrating user production environments until companies unknowingly expose confidential data and production systems, leading to severe damages. Detecting such highly complex attack patterns early on is crucial. The earlier companies identify attacks, the sooner they can take preventive measures.
Three Key Cloud Security Strategies to Effectively Combat Rampant Hacker Attacks
Given the escalating concerns surrounding cloud security incidents, how can businesses expedite their incident response? Experts well-versed in cloud security recommend implementing three strategic approaches to significantly reduce the likelihood of cloud security events:
Proactive Detection, Contextualization, and Visual Representation of Security Incidents
In the face of rapidly evolving cloud security events, ‘detection speed’ becomes a critical factor. For businesses utilizing Amazon Detective, cloud security experts recommend leveraging its Finding Groups feature to integrate security alerts from Amazon Inspector and Amazon GuardDuty. By harnessing these three AWS-managed security services, businesses can identify potential security risks swiftly, enabling prompt incident responses. Additionally, companies can utilize machine learning capabilities to visualize the alerts from Finding Groups. Through visualization, as depicted in the diagram below, businesses can quickly discern critical operational resources, network configurations, and identity settings that urgently need attention. Categorized by severity, this approach empowers businesses to respond promptly to all security incidents, ensuring comprehensive protection.”

Automation and Machine Learning: Strategies for Reducing Average Incident Response Time
In the era of machine learning (ML) and artificial intelligence (AI), employing automation and machine learning functionalities for cloud security incident response becomes a crucial strategy for accelerating incident resolution. The advantage of automating all processes lies in enabling security management teams to focus their time and energy on addressing high-priority security incidents while automated systems handle repetitive and routine tasks. In practice, when critical cloud security issues are identified using Amazon GuardDuty, a new discovery is automatically generated in AWS Security Hub. Simultaneously, based on rules set in Amazon EventBridge, the results are transmitted to AWS System Manager’s Incident Manager feature, efficiently automating the handling of security incidents and reducing the average response time.
Rapidly Enhance Incident Response Maturity
Research from CyberSeek highlights the global shortage of cybersecurity professionals, with only 69% of positions filled. Achieving incident response maturity with limited manpower underscores the importance of ‘effective security and compliance state management.’ Apart from using automated tools to centralize the efforts of cybersecurity teams, integrating multiple cloud security tools is essential. For instance, enabling AWS Security Hub and AWS Config configuration assessment tools simultaneously allows businesses to expedite incident response and audit report generation, effectively managing security incidents.
Facing ever-evolving internet threats and attacks, enterprises, whether utilizing cloud services or not, need to pay special attention to cybersecurity issues. In addition to the above strategies, businesses can review permission settings and configuration planning within their cloud environments. Nextlink Technology, as a professional AWS cloud consultant with relevant certifications in AWS data security, offers a dedicated 7×24 cloud operations team, ensuring you can face security incidents with confidence!





